Claud Xiao – 03/24/2014
Today, a Chinese security researcher find a strange iOS dynamic library file in his iOS device and post it to PEDIY[1] — the biggest security forum in China. This dynamic library, as a plugin of the Cydia Substrate framework, will replace developer ID (or promotion ID) of popular iOS advertisement SDKs in all other applications running on the infected devices, and bring promotion fee to its author. We think this sample should be classified as malware or adware. As far as we know, this is the first iOS malware based on Cydia Substrate and spread in the wild.
Cydia Substrate is a very popular runtime instrumentation framework for jailbreaked iOS devices which is commonly used by jailbreak community developers to develop powerful tools or special applications for modifing system functions or the OS interface.
This dynamic library, named “spad.dylib”, was found under the directory /Library/MobileSubstrate/DynamicLibraries/. It’s configured to be injected to all applications which use the com.apple.UIKit framework. It uses Cydia Substrate’s API to hook lots of popular advertisement SDKs’ code in all applications which use these SDK to popup advertisement or get statistics of its installation. The sample will modify the developer ID (or “promotion ID”, “refer ID”, “Publisher ID”, “Ad id”) to some specific hard-coded values. We believe these IDs are belongs to the author of this sample. By replace these IDs in other applications, all further advertisements displayed in these applications will be counted as promoted by this author. Thus he will get related promotion fee which should been originally paid to the applications’ real developers.
For example, the sample will inject the MobClick SDK’s “MobClick” class and hook the “startWithAppkey:” and “startWithAppkey:reportPolicy:channelId:” method in it, and change the related app key to “51cd7b8d56240ba38c05d087”. (See figure 1 and figure 2)
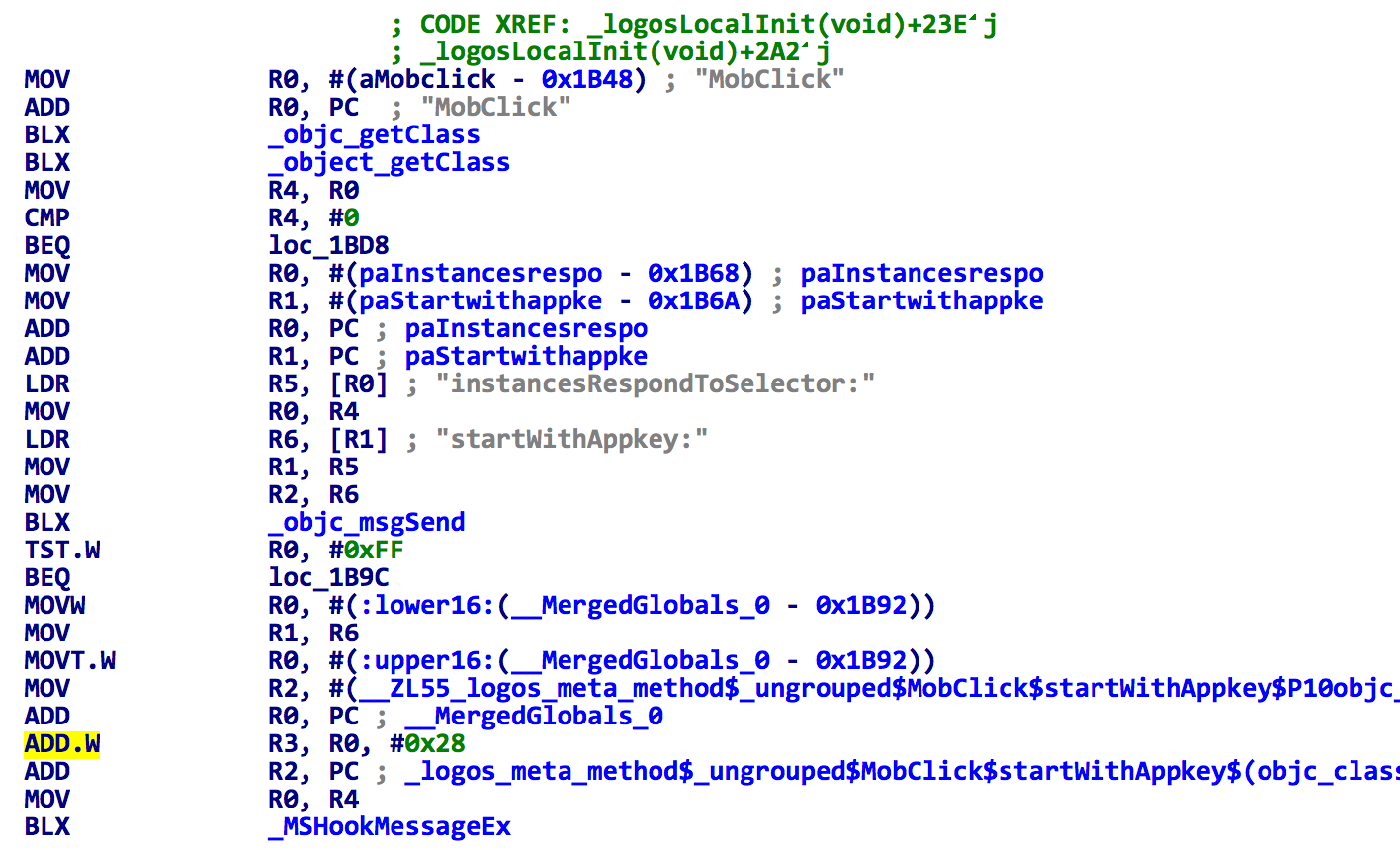
Figure 1. The spad.dylib hooks methods in MobClick SDK
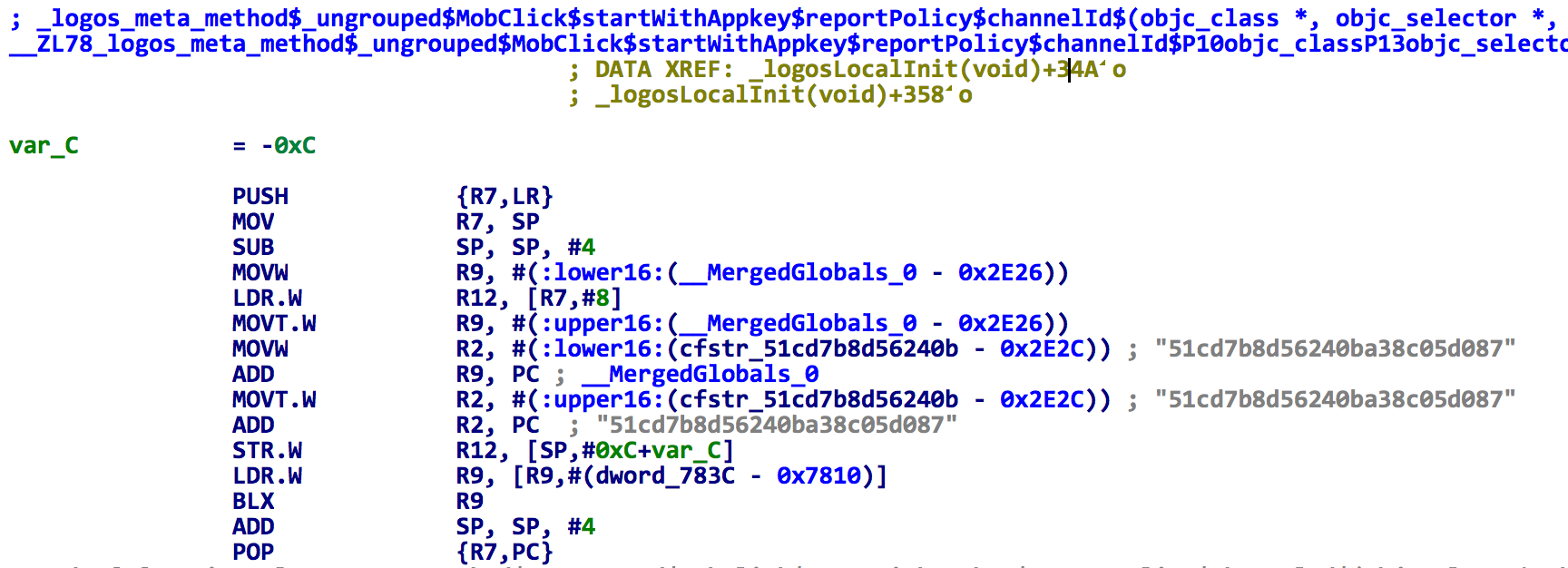
Figure 2. The spad.dylib changes app key in MobClick SDK
All advertisement SDKs targeted by the sample include:
– Youmi
– Sina Weibo
– Vpon
– Umeng MobClick
– Umeng App Union
– AdSaga
– MdotM
– InMobi
– MIX SDK
– Domob
– AdWhirl
– AdsMogo
– Google Mobile Ads SDK
– AderMob
– PolySDK
– GuoHe
– Komli Mobile
The second target in this list, Sina Weibo, is a very popular twitter-liked social network application in China but not an advertisement SDK.
This sample, spad.dylib, begin to spread in the wild at least from Dec 10, 2013, according to an iOS crash report hosted at synapticstuff.com [2]. We still don’t know how it infect the jailbreaded iOS devices. However, as the analysis above, we think it should be classified as malware or adware. Our suggest name of this familiy is iPhoneOS.Spad or iPhoneOS.AdThief.
In the past years, these’re many interesting iOS malware demo/PoC (like the Mactans and the Jekyll) written by the security researchers [3]. However, only a few iOS malware were found in the real world: Ikee, Ikee.b [4], FindAndCall [5], and Finfish. This malware becomes a new member of this short list, and is the first one based on Cydia Substrate.
UPDATE 03/25/2014
1. I’ve submitted the samples to the contagiominidump, while they havn’t published them yet. You can also download them from:
http://blog.claudxiao.net/files/ios_spad.zip
2. Here’re some statistics of the malware’s infection come from one of my private channels:
i. Infected devices: ~75k
ii. Total activate times: ~22m
iii. Daily activate times (around 3/20/2014): ~22k
UPDATE 03/26/2014
1. Mila has uploaded the samples to the contagiominidump:
http://contagiominidump.blogspot.com/2014/03/ios-adware-using-cydia.html
Also, I added two additional related sample files which is called/invoked by the SpAd.
2. We found a more earlier website refered to this adware, which means it’s spread from Jun 24, 2013:
http://zhidao.baidu.com/question/561894469.html
Thanks Baron tell me this.
3. A person said in the PEDIY’s post[1] that he is the author of this adware, he wrote it a year ago, and didn’t participate in its spreading.
UPDATE 03/31/2014
Axelle(@cryptax) find two more adlib in the SpAd: GuoHe and Komli Mobile. Thanks!
Reference
[1] http://bbs.pediy.com/showthread.php?p=1270415
[2] http://webservices.synapticstuff.com/guitartab/crashReport/show/24991
[3] https://sites.google.com/site/tieleiwang/
[4] http://mtc.sri.com/iPhone/
[5] https://www.securelist.com/en/blog/208193641/Find_and_Call_Leak_and_Spam